Learn the Basics
IDENTOS Overview
Digital service providers often require access to personal information in order to deliver a service to an individual. For example, a healthcare provider accesses a patient’s medical records using a digital health application.
The IDENTOS product suite enables organizations to have a secure end-to-end solution to deliver digital services to their users via portals, websites, and mobile applications.
Note: In the IDENTOS documentation, a user refers to someone who is receiving services from a digital service provider. For example, a person using a mobile banking app would be a user, and the bank providing the mobile app would be a digital service provider.
Privacy Protection
Protecting user privacy is essential when sharing personal information digitally. Individuals must be able to control who can access their information and what information they can access.
IDENTOS ensures personal information is shared securely and with the individual’s consent. When a digital service provider requests access to information (via a Client application), IDENTOS protects the user’s privacy by verifying the Client’s identity, obtaining the person’s consent to share their personal information with the Client, and confirming the Client is allowed to access the information they’ve requested. This process of granting secure access to information is called Identity and Access Management (IAM).
IDENTOS Capabilities
IDENTOS provides the following capabilities for Identity and Access Management (IAM).
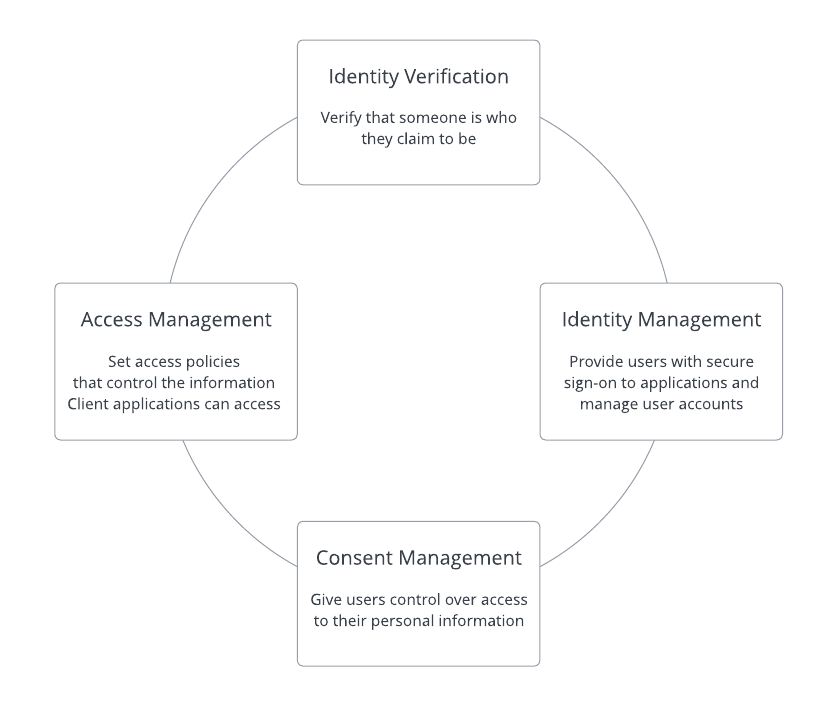
IDENTOS Identity and Access Management (IAM) Capabilities
Identity Verification
Identity verification is the process of confirming that someone is who they claim to be. This involves collecting and validating identity information for the person, such as:
- Name and date of birth
- Contact information (address, phone number, email address)
- Identity documents (driver’s license, health card, Social Security Number)
Identity verification is typically done for the purpose of linking a user with a digital account or issuing a digital credential for the user.
Identity verification can be performed at different levels of assurance (LoA). An LoA represents the trustworthiness of a user’s identity verification. For example, a user who is verified with multiple identity documents would have a higher LoA, and therefore a much stronger verification, than a user who is verified by simply filling out a form. Users with basic verification are limited in the information they can access, while strongly verified users are allowed access to sensitive information such as government or health data.
IDENTOS provides tailored identity verification solutions that allow digital service providers to safely onboard and verify new users.
Identity Management
Identity management includes authentication, which is the process of verifying that someone is allowed to sign into an application. This often includes authentication methods such as single sign-on (SSO), two-factor authentication (2FA), and multi-factor authentication (MFA). For example, someone might be required to enter a verification code in order to sign into an application, in addition to entering their username and password.
Identity management also includes creating and managing user accounts. This includes creating a user profile, managing user sessions, capturing and renewing basic terms of service, providing self-service support (e.g. a “Forgot Password” link during login), and sending notifications to users (e.g. the user’s password has been changed, the user has passed identity verification).
IDENTOS provides identity management solutions that enable simple and secure sign-on for digital service provider applications (providing an easy login experience for users) and include full user account management capabilities.
Consent Management
Consent management is the process of obtaining an individual’s consent before sharing their personal information.
The individual must clearly provide consent, for example by signing a consent form. The individual must also understand exactly what they are consenting to. They must be given a clear and comprehensive explanation of how their personal data will be used, including what information will be shared, who it will be shared with, and how it will be used.
IDENTOS consent management solutions allow users to grant or deny consent when a digital service provider asks for access to their personal information (via a Client application). Users can also revoke their consent at any time. This ensures the user is in control of who can view their personal data and exactly what they can view.
Access Management
Access management is the process of ensuring that someone can only access information that they’ve been authorized to access.
IDENTOS access management gives you full control over your environment. As the FPX administrator, you set the access policies that determine who can access the environment and what resources they are allowed to access. For example, a Client application used by a healthcare provider might be authorized to access a patient’s immunization records but not their entire medical history.
Access management is tightly linked to consent management. When a Client application requests access to a user’s protected information, the user is prompted to provide their consent.
IDENTOS Frameworks and Standards
The IDENTOS product suite uses the following authorization frameworks and standards.
OAuth 2.0
OAuth 2.0 is the industry-standard protocol for authorization and provides secure access to user data.
OpenID Connect (OIDC)
OIDC is an authentication protocol based on the OAuth 2.0 framework. This protocol provides functionality for user authentication and sign-in flows.
User Managed Access (UMA) 2.0
UMA 2.0 is an OAuth-based protocol set that manages third-party access to data and resources.
SMART on FHIR
SMART on FHIR provides a standard, universal API for accessing Electronic Health Information (EHI).
Security Assertion Markup Language (SAML)
SAML provides XML-based open-standard for transferring identity data.
Unified Data Access Profiles (UDAP)
UDAP provides a set of standards and profiles designed to enhance security and scalability in healthcare data exchange.