SMART on FHIR
The SMART on FHIR specification can be found at:
http://hl7.org/fhir/smart-app-launch/
FPX SMART On FHIR Profile
SMART on FHIR, or SoF, is an OAuth 2.0 profile. The FPX Authorization Server supports nearly all options in the 'launch sequence', but only a limited version of the 'stand-alone launch sequence'. The reason for this limitation is that the SoF specification assumes the Authorization Server can pull context-specific patient data directly from the Resource Servers it protects. However, this is not possible in many privacy-respecting FPX network configurations. As such, the only stand-alone launch sequence that is supported is the 'launch/patient' scope with the patient's own data.
Configuring an Authorization Server for SMART on FHIR
Configuring the Authorization Server generally requires three steps:
- Creating the FHIR resource definitions and scopes.
- Onboarding FHIR Resource Servers.
- Onboarding SoF client applications.
Overview: Configuration and Use
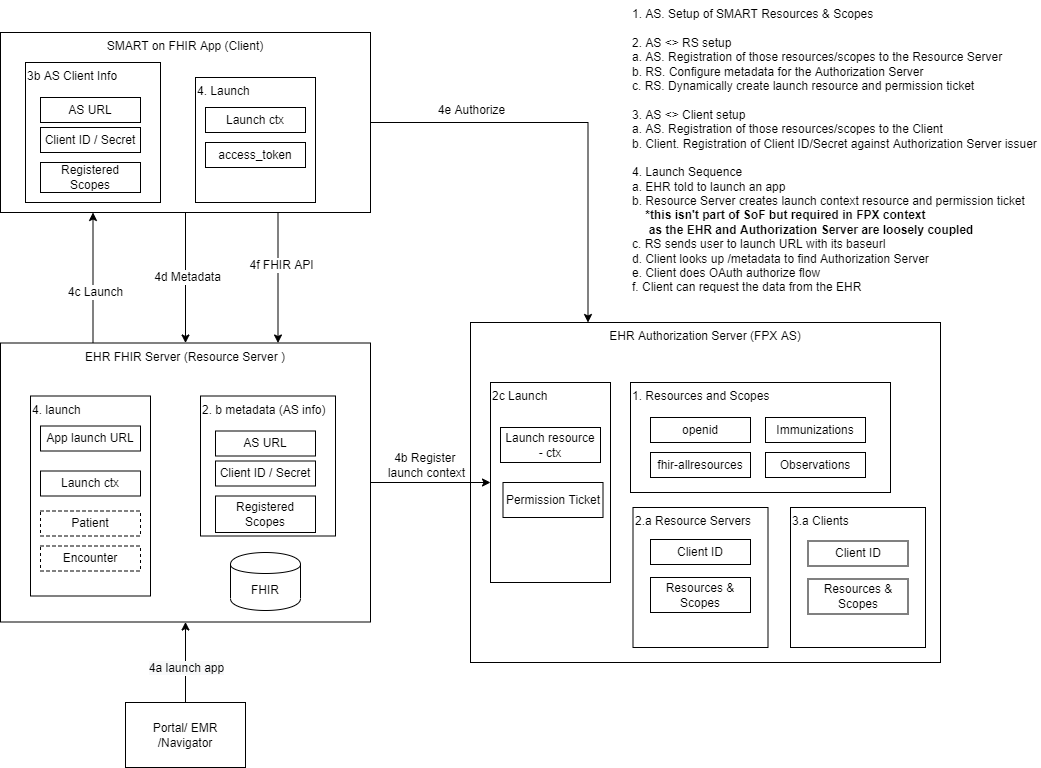
1. Resources, Resource Definitions, and Scopes
SoF scopes to FPX Resource and scopes
The SMART on FHIR specification is used to request clinical resources with resource types from http://hl7.org/implement/standards/fhir.
The SOF specification requires clinical resource access scopes to meet the following format:
( 'patient' | 'user' ) '/' ( fhir-resource | '*' ) '.' ( 'read' | 'write' | '*' ).
Examples of clinical resource access scopes would be: user/Patient.read or patient/*.*
For the rest of the section, an SoF-compliant clinical resource access scope is referred to as an SoF clinical scope, ( 'patient' | 'user' ) as the SoF requesting party scope, ( fhir-resource) as the SoF resource type, and ( 'read' | 'write' | '*' ) as the SoF resource scope.
The Authorization Server is able to map SoF OAuth scopes into resources as follows:
Use
audparameter of the authorization request to restrict the resources to the Resource Server with that base URL.For each SoF clinical scope, map it to an FPX resource and scopes as follows:
- Add the resource matching the resource type found by combining the FHIR spec base URL (default: https://www.hl7.org/fhir), the SoF resource type, and the URL suffix (default: .html). The SoF resource type of '*' is mapped to the FPX resource type of just the FHIR spec base URL.
- Add the SoF requesting party scope to that resource's requested scopes.
- Add the SoF resource scope to that resource's requested scopes. The SoF resource scope of '*' is mapped to 'read write'.
If the OAuth scope contains 'openid':
- Add the resource matching the resource type https://openid.net/specs/openid-connect-core-1_0.html to the FPX resources being requested.
- Add any requested scopes that are registered under that resource. E.g.: the scope 'openid email profile hcn user/Patient.read' would check if any of 'email', 'profile', 'hcn', 'user/Patient.read' are registered scopes.
Therefore, if an application makes an SoF request with aud 'https://www.demo-ehr.com' and scope 'openid profile patient/Patient.read patient/*.write user/Observation.* email', the Authorization Server may negotiate with the Wallet and Requesting Party for access to the following resources restricted to the Resource Server with base URL 'https://www.demo-ehr.com':
- A resource with resource type https://www.hl7.org/fhir/patient.html, scopes 'patient read' (patient/Patient.read)
- A resource with resource type https://www.hl7.org/fhir/observation.html, scopes 'user read write' (user/Observation.*)
- A resource with resource type https://openid.net/specs/openid-connect-core-1_0.html, scopes 'profile email' (openid profile email)
- A resource with resource type https://www.hl7.org/fhir, scopes 'patient write' (patient/*.write)
Registering Resource Definitions (optional)
Resource definition and scopes should be registered that meet the exact FHIR resource types, such as https://www.hl7.org/fhir/patient.html with patient, user, read, and write scopes. The resource type URL should be all lowercase. Additionally, a resource definition and scopes should be created for the openid type (https://openid.net/specs/openid-connect-core-1_0.html) if clients will request an id_token during flows.
You may create the resource definitions automatically when you create resources with the correct types.
2. Onboarding Resource Servers and Resources
Once SoF resource definitions have been created, you may onboard the SoF Resource Servers following the standard steps. Register each FHIR Resource Server with any FHIR resource types and scopes it can provide. They may also need to be registered for the Observation resource type.
Sample Resource Server Configuration
Example 1
To support openid patient/Observation.read, register the following resource against your desired Resource Server with these parameters:
resource_type: "https://www.hl7.org/fhir/Observation.html"
You should register the scopes "read" and "patient" against the resource.
To support openid which is the standard OIDC scope, register the following resource against your desired Resource Server with these parameters:
resource_type: "https://openid.net/specs/openid-connect-core-1_0.html"
You can register any specific OIDC scopes you would like on this resource. Common scopes are "profile" and "email".
- other fields filled in the same manner as a standard resource
Example 2
The SMART application will request patient/*.*
To support patient/*.*, register the following resource with these parameters:
resource_type: "https://www.hl7.org/fhir"
- other fields filled in the same manner as a standard resource
You will also need to register the scopes "read", "write", and "patient" on the resource.
3. Onboarding Clients
No unique customization is required when onboarding SoF Clients. Provide client authentication details, redirect URIs, and other metadata.
Ensure that they have a capability ticket that contains all SoF resource definitions and scopes that they will request. This may include the Observation resource type if they require id_tokens. Although SoF applications will not use the capability ticket, it will give them the privileges required to request the underlying resources through SoF OAuth 2.0 flows.
4. Launch Sequence Flow
4.a Request EHR launches App
To provide a launch parameter to the SMART-APP a launch context needs to be created on the EHR server. To kick off Launch-Context Creation, launch details (such as which patient and/or encounter is currently open in the context) and the smart-app's launch URL must be provided to the /launch-app endpoint of the EHR.
Request:
POST to "https://{resource-server-base-url}/launch-app
{
"launch_params" : {
"patient": "https://r3.smarthealthit.org/Patient/1a8ba720-7e93-4884-8d54-eaff2986e457",
"encounter": "https://r3.smarthealthit.org/Encounter/ifj05j5945g0",
"need_patient_banner": false,
"intent":"reconcile-medications"
},
"launch_url": "http://{smart-app-launch-url}"
}
4.b EHR creates launch context with Authorization Server
Create launch context resource
Request: The EHR takes in the launch details and makes a request to the Authorization Server to register a launch resource with the scopes representing:
Headers: Authorization : Bearer PAT
{
type: http://hl7.org/fhir/smart-app-launch/scopes-and-launch-context/index.html
name: "Launch-Context"
resource_scopes:[
"patient.anon/d89954f0ffj",
"encounter.anon/ifj05j5945g0",
"need_patient_banner.true",
"intent.reconcile-medications",
]
}
Response:
{
_id:{resource-id} ( this is the id of the "launch" resource that was just created)
user_access_policy_url:"http://authserverURL/registry/resource/{resource-id}/policy"
}
Create permission ticket (passed as launch parameter to SMART App)
Request:
Headers: Authorization : Bearer PAT
POST to http://authserver-base-url/transaction/permission
{
"resource_id": "{resource-id-created}",
"resource_scopes":
[
"patient.anon/d89954f0ffj",
"encounter.anon/ifj05j5945g0",
"need_patient_banner.true",
"intent.reconcile-medications",
]
}
Response:
{
"ticket": "b78bed5a-c5b8-45b2-b68b-22dbb137d664"
}
4.c EHR launches App
EHR redirects to launch URL of SMART-APP with a "launch" parameter appended.
redirect: "http://{smart-app-launch-url}?launch=b78bed5a-c5b8-45b2-b68b-22dbb137d664"
4.d App requests EHR metadata
SMART-APP needs location of Authorization and Token Endpoints. It makes a call to the metadata endpoint exposed by the EHR server.
Request :
GET:
http://{resource-server-base-url}/api/.well-known/smart-configuration
Response :
{
"response_types_supported": [
"code",
"code id_token",
"id_token",
"refresh_token"
],
"capabilities": [
"launch-ehr",
"client-public",
"client-confidential-symmetric",
"context-ehr-patient",
"sso-openid-connect"
],
"management_endpoint": "http://{authorization-server-base-url}/manage",
"introspection_endpoint": "http://{authorization-server-base-url}/transaction/introspect",
"revocation_endpoint": "http://{authorization-server-base-url}/transaction/revocation",
"token_endpoint_auth_methods_supported": [
"client_secret_basic"
],
"registration_endpoint": "{authorization-server-base-url}/register",
"scopes_supported": [
"openid",
"profile",
"launch",
"launch/patient",
"patient/*.*",
"user/*.*",
"offline_access"
],
"authorization_endpoint": "https://{authorization-server-base-url}/oauth2/authenticate",
"token_endpoint": "https://{authorization-server-base-url}/transaction/token"
}
The SMART App uses the authorization and token endpoints from the response.
4.e App requests authorization
SMART-APP redirects to the authorization endpoint of the Authorization Server received from metadata call and appends client-id, scope, redirect_uri, aud, state, and launch parameter to it.
Request/Redirect:
https://{authorization-server-base-url}/oauth2/authenticate?response_type=code&client_id=growth_chart&scope=patient%2FObservation.read%20patient%2FPatient.read%20launch&redirect_uri=http%3A%2F%2F{smart-app-redirect-url}&aud=http%3A%2F%2F{resource-server-base-url}%3A8086%2Fapi&state=4vveoYexhuJRo3Zw&launch=9928fb1e-b2e0-408e-95b8-7d1aa1c0e1be
- User is redirected to "Select a Broker Page".
- Select Appropriate Broker.
- User is redirected to a screen containing a QR code.
- Scan QR code using the Navigator installed on your personal device.
- After giving consent, the Authorization Server redirects to the SMART-APP with an Authorization Code which it uses to request a token from the Token Endpoint of the Authorization Server.
Redirect back to SMART-APP:
https://{smart-app-redirect-url}?code=e88f3c95-f05d-4525-8c12-493ae5a677c9&state=4vveoYexhuJRo3Zw
SMART-APP makes a request for an Access Token using Authorization Code provided by Authorization Server
Request:
POST to https://{authorization-server-base-url}/transaction/token
Headers: Authorization: Basic Auth
{
"grant_type": "authorization_code",
"code":"e88f3c95-f05d-4525-8c12-493ae5a677c9"
"redirect_uri":"https://{smart-app-redirect-url}"
}
Response:
{
"access_token":"eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJleUpoYkdjaU9pSklVekkxTmlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKeVpYTnZkWEpqWlY5cFpDSTZJazlpYzJWeWRtRjBhVzl1SWl3aWMzVmlJam9pV2pkR1JuZGhWWHBqZFhKUFdraHlVazFETVZNMmJGaEdaVlp4TlRBMFdFUlpha2xJUTBVMFNuaGhZMjUyUVVoUFFqTldSbU14VW5kUlRVcHVTMjlVVVNJc0ltZHlZVzUwWldSZmMyTnZjR1Z6SWpwYkluQmhkR2xsYm5RaUxDSnlaV0ZrSWwwc0ltRjFaQ0k2SW1oMGRIQTZYQzljTHpFNU1pNHhOamd1TnpVdU1UTXlPamd3T0RaY0wyRndhU0lzSW5SNWNHVWlPaUpRWlhKdGFYTnphVzl1SWl3aVkyeHBaVzUwWDJsa0lqb2ljMjFoY25RdGNuTXRZMnhwWlc1MExXbGtJaXdpYVhOeklqb2lUbUYyYVdkaGRHOXlJRmRoYkd4bGRDSjkuV2l6NDZsdlJYNGZMV3dZSEIxal9KMnY0ckJhY285eDJRaDRhWnZYRkVqMCIsImF1ZCI6Imh0dHA6XC9cLzE5Mi4xNjguNzUuMTMyOjgwODZcL2FwaSIsInBlcm1pc3Npb25zIjpbeyJzdWIiOiJleUpoYkdjaU9pSklVekkxTmlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKeVpYTnZkWEpqWlY5cFpDSTZJazlpYzJWeWRtRjBhVzl1SWl3aWMzVmlJam9pV2pkR1JuZGhWWHBqZFhKUFdraHlVazFETVZNMmJGaEdaVlp4TlRBMFdFUlpha2xJUTBVMFNuaGhZMjUyUVVoUFFqTldSbU14VW5kUlRVcHVTMjlVVVNJc0ltZHlZVzUwWldSZmMyTnZjR1Z6SWpwYkluQmhkR2xsYm5RaUxDSnlaV0ZrSWwwc0ltRjFaQ0k2SW1oMGRIQTZYQzljTHpFNU1pNHhOamd1TnpVdU1UTXlPamd3T0RaY0wyRndhU0lzSW5SNWNHVWlPaUpRWlhKdGFYTnphVzl1SWl3aVkyeHBaVzUwWDJsa0lqb2ljMjFoY25RdGNuTXRZMnhwWlc1MExXbGtJaXdpYVhOeklqb2lUbUYyYVdkaGRHOXlJRmRoYkd4bGRDSjkuV2l6NDZsdlJYNGZMV3dZSEIxal9KMnY0ckJhY285eDJRaDRhWnZYRkVqMCIsInJlc291cmNlX3Njb3BlcyI6WyJwYXRpZW50IiwicmVhZCJdLCJyZXNvdXJjZV90eXBlIjoiMTIxMDAiLCJyZXNvdXJjZV9pZCI6Ik9ic2VydmF0aW9uIiwiZXhwIjoxNTczMjQ0Njg0fSx7InN1YiI6ImV5SmhiR2NpT2lKSVV6STFOaUlzSW5SNWNDSTZJa3BYVkNKOS5leUp5WlhOdmRYSmpaVjlwWkNJNklsQmhkR2xsYm5RaUxDSnpkV0lpT2lKbk1tZGpaMVp3TlhkWGRsSnpVR051VjJWTldURjJNR2xOVjA5U2VXUXdSVU5NV21WVmIyeDJWR3hqYjNKSGVGTllWWFEyYlRKQk0xbHlNV0pGV0RsWUlpd2laM0poYm5SbFpGOXpZMjl3WlhNaU9sc2ljbVZoWkNJc0luQmhkR2xsYm5RaVhTd2lZWFZrSWpvaWFIUjBjRHBjTDF3dk1Ua3lMakUyT0M0M05TNHhNekk2T0RBNE5sd3ZZWEJwSWl3aWRIbHdaU0k2SWxCbGNtMXBjM05wYjI0aUxDSmpiR2xsYm5SZmFXUWlPaUp6YldGeWRDMXljeTFqYkdsbGJuUXRhV1FpTENKcGMzTWlPaUpPWVhacFoyRjBiM0lnVjJGc2JHVjBJbjAuTTJmc29kWmN2VW9yeTlwTVN1ZUd6M2FYUWN3anBVeHdpZVN0UXJneVg3MCIsInJlc291cmNlX3Njb3BlcyI6WyJwYXRpZW50IiwicmVhZCJdLCJyZXNvdXJjZV90eXBlIjoiOTUwMCIsInJlc291cmNlX2lkIjoiUGF0aWVudCIsImV4cCI6MTU3MzI0NDY4NH1dLCJpc3MiOiJodHRwOlwvXC8xOTIuMTY4Ljc1LjEzMjo4MDg0IiwiZXhwIjoxNTczMjQ0Njg0LCJpYXQiOjE1NzMyNDM3MDIsImNsaWVudF9pZCI6InNtYXJ0LXJzLWNsaWVudC1pZCJ9.lNC_NeeFCEqIulnuCugiNw1nCdJXk6FUJX_A49oj32AVyFfRih41So4ieKJb4buelnGLccZ0_dZ4eR0PE0a9uLOKI6ENypjXNkClz_ALudA1-ceSCSKlCB6CT92e7N2cGBRRIo7AAK2k0IdhlO_9bqwBtvS6c7NjSvcMApvEwqDkHbTg2oVa_KPRzRLICTXI1ZMrc8sGvObhrbopMiemqLwHtY-_gIAmlKgmkoTJAskqTKdUEpUz0udQ_kPDn3nJZ4l5MPzaVDyzlRzw8-WzYrqBE0nH7R-ikxw3o_9zPWVr3ZcpSiah0AnoZSHiVKfs5x6A3mKvKz8WNuIlUm0FaA"
"expires_in": "117219"
"token_type":"Bearer"
"refresh_token":"a11a49ad-b225-4adf-8c0b-ad3f8574d977"
"id_token":"eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJhdWQiOiJzbWFydC1ycy1jbGllbnQtaWQiLCJwZXJtaXNzaW9ucyI6eyJPYnNlcnZhdGlvbiI6ImV5SmhiR2NpT2lKSVV6STFOaUlzSW5SNWNDSTZJa3BYVkNKOS5leUp5WlhOdmRYSmpaVjlwWkNJNklrOWljMlZ5ZG1GMGFXOXVJaXdpYzNWaUlqb2lXamRHUm5kaFZYcGpkWEpQV2toeVVrMURNVk0yYkZoR1pWWnhOVEEwV0VSWmFrbElRMFUwU25oaFkyNTJRVWhQUWpOV1JtTXhVbmRSVFVwdVMyOVVVU0lzSW1keVlXNTBaV1JmYzJOdmNHVnpJanBiSW5CaGRHbGxiblFpTENKeVpXRmtJbDBzSW1GMVpDSTZJbWgwZEhBNlhDOWNMekU1TWk0eE5qZ3VOelV1TVRNeU9qZ3dPRFpjTDJGd2FTSXNJblI1Y0dVaU9pSlFaWEp0YVhOemFXOXVJaXdpWTJ4cFpXNTBYMmxrSWpvaWMyMWhjblF0Y25NdFkyeHBaVzUwTFdsa0lpd2lhWE56SWpvaVRtRjJhV2RoZEc5eUlGZGhiR3hsZENKOS5XaXo0Nmx2Ulg0ZkxXd1lIQjFqX0oydjRyQmFjbzl4MlFoNGFadlhGRWowIiwiUGF0aWVudCI6ImV5SmhiR2NpT2lKSVV6STFOaUlzSW5SNWNDSTZJa3BYVkNKOS5leUp5WlhOdmRYSmpaVjlwWkNJNklsQmhkR2xsYm5RaUxDSnpkV0lpT2lKbk1tZGpaMVp3TlhkWGRsSnpVR051VjJWTldURjJNR2xOVjA5U2VXUXdSVU5NV21WVmIyeDJWR3hqYjNKSGVGTllWWFEyYlRKQk0xbHlNV0pGV0RsWUlpd2laM0poYm5SbFpGOXpZMjl3WlhNaU9sc2ljbVZoWkNJc0luQmhkR2xsYm5RaVhTd2lZWFZrSWpvaWFIUjBjRHBjTDF3dk1Ua3lMakUyT0M0M05TNHhNekk2T0RBNE5sd3ZZWEJwSWl3aWRIbHdaU0k2SWxCbGNtMXBjM05wYjI0aUxDSmpiR2xsYm5SZmFXUWlPaUp6YldGeWRDMXljeTFqYkdsbGJuUXRhV1FpTENKcGMzTWlPaUpPWVhacFoyRjBiM0lnVjJGc2JHVjBJbjAuTTJmc29kWmN2VW9yeTlwTVN1ZUd6M2FYUWN3anBVeHdpZVN0UXJneVg3MCJ9LCJpc3MiOiJodHRwOlwvXC8xOTIuMTY4Ljc1LjEzMjo4MDgxIiwiZXhwIjoxNTkxMjQzNzAzLCJpYXQiOjE1NzMyNDM3MDN9.mk05r_aOuamr_1qSF6if04k2wu2GzHBwgiPDcfwwh4LMZ__I2qR-FZx0pHtavAlGEez2bJ1VItBoDjYcIqpYbZyuhpTpZWz6Ia2i_CXQNXCmv8McdG1DpdiGJ8Xjz97zl7k0Ygv1jWtkKeJsX4kKrSExdN5Nmbcd1y1z9E0WjaIwPRmSielzqKKmPytKzhJdINFEfoIC9Cb2wsn4nkZQZZAWDAsI2UI_MCjatuzzwK2KaEDmIgffQrq57RUnhG55olvtWg3uiw4ogXeaUDIo1lMoooMEIkVpEDwmiKnt7YFawV3mqIylnBdlhbMuNWZTvOwQFGD08H6imB7zWmhzEw"
"scope": "patient/Patient.read patient/Observation.read"
"encounter": "anon/673c443af0ac10d38bcae2abd1c096ccdcda20949010f2b6715c5a0e7e8b2424"
"patient": "anon/905256a6de5a9df7b461b320c966461741ba11ad7d100ab32f4b615215c642c4"
"intent": "reconcile-medications"
"need_patient_banner": "false"
}
4.f App requests FHIR resource
SMART-APP requests resources with an Access Token Request 1:
Authorization: Bearer eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJleUpoYkdjaU9pSklVekkxTmlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKeVpYTnZkWEpqWlY5cFpDSTZJazlpYzJWeWRtRjBhVzl1SWl3aWMzVmlJam9pV0V0SU5FRTBXRk0xUkRkbVEwcE9RMFp2UzBkWU1XODJXbTg1V2tKTU0ycFNlamM1ZVdWeU1GbHJSRFJVYVZCblpFUTNWVlpwWkRSMFdHNHdlbVJLWVNJc0ltZHlZVzUwWldSZmMyTnZjR1Z6SWpwYkluSmxZV1FpTENKd1lYUnBaVzUwSWwwc0ltRjFaQ0k2SW1oMGRIQTZYQzljTHpFNU1pNHhOamd1TnpVdU1UWXpPamd3T0RaY0wyRndhU0lzSW5SNWNHVWlPaUpRWlhKdGFYTnphVzl1SWl3aVkyeHBaVzUwWDJsa0lqb2laM0p2ZDNSb0xXTm9ZWEowTFdGd2NDSXNJbWx6Y3lJNklrNWhkbWxuWVhSdmNpQlhZV3hzWlhRaWZRLk9fakZpNm9yYTNMNUcxQ3BZNXdTdkloUm1kblBXWjlSc3dCZ3hLdWxBbTgiLCJhdWQiOiJodHRwOlwvXC8xOTIuMTY4Ljc1LjE2Mzo4MDg2XC9hcGkiLCJwZXJtaXNzaW9ucyI6W3sic3ViIjoiZXlKaGJHY2lPaUpJVXpJMU5pSXNJblI1Y0NJNklrcFhWQ0o5LmV5SnlaWE52ZFhKalpWOXBaQ0k2SWs5aWMyVnlkbUYwYVc5dUlpd2ljM1ZpSWpvaVdFdElORUUwV0ZNMVJEZG1RMHBPUTBadlMwZFlNVzgyV204NVdrSk1NMnBTZWpjNWVXVnlNRmxyUkRSVWFWQm5aRVEzVlZacFpEUjBXRzR3ZW1SS1lTSXNJbWR5WVc1MFpXUmZjMk52Y0dWeklqcGJJbkpsWVdRaUxDSndZWFJwWlc1MElsMHNJbUYxWkNJNkltaDBkSEE2WEM5Y0x6RTVNaTR4TmpndU56VXVNVFl6T2pnd09EWmNMMkZ3YVNJc0luUjVjR1VpT2lKUVpYSnRhWE56YVc5dUlpd2lZMnhwWlc1MFgybGtJam9pWjNKdmQzUm9MV05vWVhKMExXRndjQ0lzSW1semN5STZJazVoZG1sbllYUnZjaUJYWVd4c1pYUWlmUS5PX2pGaTZvcmEzTDVHMUNwWTV3U3ZJaFJtZG5QV1o5UnN3Qmd4S3VsQW04IiwicmVzb3VyY2Vfc2NvcGVzIjpbInBhdGllbnQiLCJyZWFkIl0sInJlc291cmNlX3R5cGUiOiJodHRwczpcL1wvb2JzZXJ2YXRpb24iLCJyZXNvdXJjZV9pZCI6Ik9ic2VydmF0aW9uIiwiZXhwIjoxNTczMjM5NjM5fSx7InN1YiI6ImV5SmhiR2NpT2lKSVV6STFOaUlzSW5SNWNDSTZJa3BYVkNKOS5leUp5WlhOdmRYSmpaVjlwWkNJNklsQmhkR2xsYm5RaUxDSnpkV0lpT2lKb1psaEpkalo0VkRoVlVHRk9jRWhFVVc5UFZIaHJZM04xU1hCclIweGtOV3M1YTBGNGIwdGxSRTlXY1RoMlpEUkpja1ZDVFZGR1dXdDZaMUUwVjFKd0lpd2laM0poYm5SbFpGOXpZMjl3WlhNaU9sc2ljbVZoWkNJc0luQmhkR2xsYm5RaVhTd2lZWFZrSWpvaWFIUjBjRHBjTDF3dk1Ua3lMakUyT0M0M05TNHhOak02T0RBNE5sd3ZZWEJwSWl3aWRIbHdaU0k2SWxCbGNtMXBjM05wYjI0aUxDSmpiR2xsYm5SZmFXUWlPaUpuY205M2RHZ3RZMmhoY25RdFlYQndJaXdpYVhOeklqb2lUbUYyYVdkaGRHOXlJRmRoYkd4bGRDSjkuemtRMjItNlN2M0tSTm1uUF9sVEJkWEpKeVVpc1ZGSWc5ZFEwTFhleFcxQSIsInJlc291cmNlX3Njb3BlcyI6WyJwYXRpZW50IiwicmVhZCJdLCJyZXNvdXJjZV90eXBlIjoiaHR0cHM6XC9cL3BhdGllbnQiLCJyZXNvdXJjZV9pZCI6IlBhdGllbnQiLCJleHAiOjE1NzMyMzk2Mzl9XSwiaXNzIjoiaHR0cDpcL1wvMTkyLjE2OC43NS4xNjM6ODA4NCIsImV4cCI6MTU3MzIzOTYzOSwiaWF0IjoxNTczMjM3ODI2LCJjbGllbnRfaWQiOiJncm93dGhfY2hhcnQifQ.bhUpm5oOxM43sJsiYroYs395uMNrEzA-pXozA0UEJiLw3EvB9jBpo4srZ6lmY7RReGvs6HTVCjnPXsgOt6xdiCttAhbAQlR2q3udAHEUWU2M--WW8YSEqvfvysK_iZqTHHbIDmwOsn6HSeQK0A8rLjzzwP_v8mP1sibrVxRYZLy_raU5WIaKwCbPLtSf9pcaMyGpZV6EZOkUQ5myUvyedvKdMl35BzVK-VeIl66wnFDVOC5JLKnnv3oyfKbVAiIEMHZwmnwWuw_CZWH3EN_CAGu1Le73QiWHjR_7uy0Bc-krJqP3lG-o1JNObSvrES2XIuXR_pJ7snGcaX6yFKmSFQ
GET https://{resource-server-base-url}/api/Patient/anon/673c443af0ac10d38bcae2abd1c096ccdcda20949010f2b6715c5a0e7e8b2424
Response:
Patient FHIR Bundle
Request 2:
Authorization: Bearer eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJleUpoYkdjaU9pSklVekkxTmlJc0luUjVjQ0k2SWtwWFZDSjkuZXlKeVpYTnZkWEpqWlY5cFpDSTZJazlpYzJWeWRtRjBhVzl1SWl3aWMzVmlJam9pV0V0SU5FRTBXRk0xUkRkbVEwcE9RMFp2UzBkWU1XODJXbTg1V2tKTU0ycFNlamM1ZVdWeU1GbHJSRFJVYVZCblpFUTNWVlpwWkRSMFdHNHdlbVJLWVNJc0ltZHlZVzUwWldSZmMyTnZjR1Z6SWpwYkluSmxZV1FpTENKd1lYUnBaVzUwSWwwc0ltRjFaQ0k2SW1oMGRIQTZYQzljTHpFNU1pNHhOamd1TnpVdU1UWXpPamd3T0RaY0wyRndhU0lzSW5SNWNHVWlPaUpRWlhKdGFYTnphVzl1SWl3aVkyeHBaVzUwWDJsa0lqb2laM0p2ZDNSb0xXTm9ZWEowTFdGd2NDSXNJbWx6Y3lJNklrNWhkbWxuWVhSdmNpQlhZV3hzWlhRaWZRLk9fakZpNm9yYTNMNUcxQ3BZNXdTdkloUm1kblBXWjlSc3dCZ3hLdWxBbTgiLCJhdWQiOiJodHRwOlwvXC8xOTIuMTY4Ljc1LjE2Mzo4MDg2XC9hcGkiLCJwZXJtaXNzaW9ucyI6W3sic3ViIjoiZXlKaGJHY2lPaUpJVXpJMU5pSXNJblI1Y0NJNklrcFhWQ0o5LmV5SnlaWE52ZFhKalpWOXBaQ0k2SWs5aWMyVnlkbUYwYVc5dUlpd2ljM1ZpSWpvaVdFdElORUUwV0ZNMVJEZG1RMHBPUTBadlMwZFlNVzgyV204NVdrSk1NMnBTZWpjNWVXVnlNRmxyUkRSVWFWQm5aRVEzVlZacFpEUjBXRzR3ZW1SS1lTSXNJbWR5WVc1MFpXUmZjMk52Y0dWeklqcGJJbkpsWVdRaUxDSndZWFJwWlc1MElsMHNJbUYxWkNJNkltaDBkSEE2WEM5Y0x6RTVNaTR4TmpndU56VXVNVFl6T2pnd09EWmNMMkZ3YVNJc0luUjVjR1VpT2lKUVpYSnRhWE56YVc5dUlpd2lZMnhwWlc1MFgybGtJam9pWjNKdmQzUm9MV05vWVhKMExXRndjQ0lzSW1semN5STZJazVoZG1sbllYUnZjaUJYWVd4c1pYUWlmUS5PX2pGaTZvcmEzTDVHMUNwWTV3U3ZJaFJtZG5QV1o5UnN3Qmd4S3VsQW04IiwicmVzb3VyY2Vfc2NvcGVzIjpbInBhdGllbnQiLCJyZWFkIl0sInJlc291cmNlX3R5cGUiOiJodHRwczpcL1wvb2JzZXJ2YXRpb24iLCJyZXNvdXJjZV9pZCI6Ik9ic2VydmF0aW9uIiwiZXhwIjoxNTczMjM5NjM5fSx7InN1YiI6ImV5SmhiR2NpT2lKSVV6STFOaUlzSW5SNWNDSTZJa3BYVkNKOS5leUp5WlhOdmRYSmpaVjlwWkNJNklsQmhkR2xsYm5RaUxDSnpkV0lpT2lKb1psaEpkalo0VkRoVlVHRk9jRWhFVVc5UFZIaHJZM04xU1hCclIweGtOV3M1YTBGNGIwdGxSRTlXY1RoMlpEUkpja1ZDVFZGR1dXdDZaMUUwVjFKd0lpd2laM0poYm5SbFpGOXpZMjl3WlhNaU9sc2ljbVZoWkNJc0luQmhkR2xsYm5RaVhTd2lZWFZrSWpvaWFIUjBjRHBjTDF3dk1Ua3lMakUyT0M0M05TNHhOak02T0RBNE5sd3ZZWEJwSWl3aWRIbHdaU0k2SWxCbGNtMXBjM05wYjI0aUxDSmpiR2xsYm5SZmFXUWlPaUpuY205M2RHZ3RZMmhoY25RdFlYQndJaXdpYVhOeklqb2lUbUYyYVdkaGRHOXlJRmRoYkd4bGRDSjkuemtRMjItNlN2M0tSTm1uUF9sVEJkWEpKeVVpc1ZGSWc5ZFEwTFhleFcxQSIsInJlc291cmNlX3Njb3BlcyI6WyJwYXRpZW50IiwicmVhZCJdLCJyZXNvdXJjZV90eXBlIjoiaHR0cHM6XC9cL3BhdGllbnQiLCJyZXNvdXJjZV9pZCI6IlBhdGllbnQiLCJleHAiOjE1NzMyMzk2Mzl9XSwiaXNzIjoiaHR0cDpcL1wvMTkyLjE2OC43NS4xNjM6ODA4NCIsImV4cCI6MTU3MzIzOTYzOSwiaWF0IjoxNTczMjM3ODI2LCJjbGllbnRfaWQiOiJncm93dGhfY2hhcnQifQ.bhUpm5oOxM43sJsiYroYs395uMNrEzA-pXozA0UEJiLw3EvB9jBpo4srZ6lmY7RReGvs6HTVCjnPXsgOt6xdiCttAhbAQlR2q3udAHEUWU2M--WW8YSEqvfvysK_iZqTHHbIDmwOsn6HSeQK0A8rLjzzwP_v8mP1sibrVxRYZLy_raU5WIaKwCbPLtSf9pcaMyGpZV6EZOkUQ5myUvyedvKdMl35BzVK-VeIl66wnFDVOC5JLKnnv3oyfKbVAiIEMHZwmnwWuw_CZWH3EN_CAGu1Le73QiWHjR_7uy0Bc-krJqP3lG-o1JNObSvrES2XIuXR_pJ7snGcaX6yFKmSFQ
GET https://{resource-server-base-url}/api/Observation
Response:
Observation FHIR Bundle
4. Alternative 'Standalone Launch Sequence'
If the Client requires launch details in a standalone sequence, they can only use the 'launch/patient' scope. This will be returned in the patient parameter, with the ROT substituted for the real patient id. The EHR Resource Server must be able to translate ROT values present in client requests. This is not within the scope of this guide.
Example:
- Client makes an OAuth authorization request including the scope 'launch/patient'.
- Patient with ID 'abc' matches with the EHR through the Wallet and is given an ROT value of 'xyz'.
- Client receives extra parameter at the token endpoint 'patient=xyz'.
- Client requests patient data that the EHR_URL/Patient/xyz or EHR_URL/Patient?_id=xyz.
- The Resource Server translates request into EHR_URL/Patient/abc or EHR_URL/Patient?_id=abc and returns the correct data.
Common Errors
If a SoF scope is mapped to a resource definition that is not in the database, or the Resource Server is not authorized to provide those resource definitions and scopes, an 'Invalid Scope Error' will be returned to the user during initial authorization.
If the client does not provide an 'aud' parameter, or the 'aud' does not match a Resource Server's base URL, an 'Invalid Request Error' will be returned to the user during initial authorization.
If the client does have have the right to request a resource definition, an 'Invalid Request Error' will be returned to the user after the Wallet negotiates permissions with them.