Integrating a Client with the Authorization Server
The Client (also known as the consumer or service provider) wants to provide services to end-users. To this end, they often require attributes and access to APIs from third parties. For example, in order to create a new trusted "doctor" account, the Client may need a doctor's provincial/state license number from an FHIR Repository hosted by a trusted provincial/state hospital. The FPX (Federated Privacy Exchange) network allows a Client to ask for vetted, trustworthy sources for the resources they need, along with the authorization to retrieve them. Rather than set up many connections with many resource servers, a Client only needs to connect to a single entity, the FPX Authorization Server (AS). The interface exposed to the Client supports OAuth 2.0 protocol as well as OAuth extensions such as User-Managed Access (UMA) 2.0 and OpenID Connect (OIDC).
Abstract Flow
The Client follows an OAuth 2.0 Authorization pattern (see Figure 1). First, it requests access to resources specified in one of their capability tickets (set of resources) from the Authorization Server (1). After the end-user interacts with the Authorization Server to fulfill the ticket, the Client receives a callback with an authorization grant (2). The Client can redeem the ticket for a set of access tokens, and then use those access tokens directly with the resource server (3) to receive the protected resource owned by the end-user (4). This chapter will cover all of these steps from the perspective of an FPX UMA flow using a Capability Ticket, a standard OAuth 2.0 or an OIDC flow using the Authorization Code grant type.
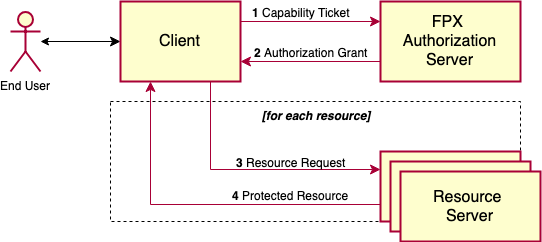
Steps involved in a typical end-to-end execution of an FPX UMA, OAuth or OIDC flow are:
- Abstract Flow
- 1. Register and Configure Client
- 2. Authorize Client
- 3. Client Callback and Authorization Code from the Authorization Server
- 4. Access Token Request
- Resource Server API
- Token Revocation
- References
1. Register and Configure Client
Before the Client can issue a capability ticket request to the Authorization Server, there are two prerequisite steps:
- Client Registration and
- Capability Ticket Registration
Client Registration
The Client must be registered as an OAuth 2.0 Client with the Authorization Server which includes a client identifier and the location of the client's publicly exposed JSON Web Key Set. It is possible to provide a shared secret to the client. However, this is strongly discouraged in production environments. Additionally, the client will need to provide the list of redirect URLs that are allowed to receive the callback from the Authorization Server. For more details on how to register a new Client, refer to Configuring a Client via API
Capability Ticket Registration
A capability ticket represents a set of resource types and scopes that the Client can request from an end-user, along with a public name and purpose for the resources within the request. When the Client makes an authorization request, it includes one of its registered tickets.
For example, a digital prescribing app may request a capability ticket to be created that allows them to request access to both the FHIR repository type, and the FHIR Practitioner resource type, both with the scope "read". These resource types are required to verify that the end-user is a valid physician in the region, and grant access to pull clinical data. The network operator would review and register a unique capability ticket ID for the Client to request that specific set of resource types and scopes from the user.
If the client chooses to integrate with the Authorization Server using OAuth, the ticket must still be registered and the 'id' of the ticket will be used as the value for the scope parameter for any OAuth calls made to the AS.
2. Authorize Client
During an authorization transaction, the Client uses two endpoints at the Authorization Server:
- An end-user-facing endpoint that users will be redirected to complete an authorization request, and
- A back-channel request to receive access tokens after the request is completed.
The client may also use the well-known (i.e. metadata) endpoints at the Authorization Server to determine the public configuration of the Authorization Server. Depending on the flow selected (FPX UMA, OAuth, or OIDC), the calls made for the Authorize Client step will differ slightly.
- FPX UMA 2.0
- OAuth 2.0
- OIDC
GET /transaction/authorize
The Client directs a user to complete an authorization request at the Authorization Server through their web browser, typically via a hyperlink or directly redirecting the user to it. The request includes a UMA 2.0 ticket and required OAuth 2.0 parameters. Once the request is processed and verified by the Authorization Server (an instantaneous process), the user will be redirected to the Wallet configured at the server to authorize the disclosure of the requested resources.
https://{AuthorizationServer_base_url}/transaction/authorize?&ticket=read-ticket&client_id=fp_client_id&state=1654184497&claims_redirect_uri={Client_redirect_url}
| Parameter | Required | Description |
|---|---|---|
| ticket | YES | Identifier of registered capability ticket. |
| claims_redirect_uri | YES | One of the registered redirect URIs. |
| client_id | YES | OAuth 2.0 Client ID. |
| state | YES | Opaque string to associate the authentication request during the callback. |
| login_hint | NO | Optional Wallet ID to pre-select a specific Wallet where multiple may be configured at the Authorization Server. |
GET /oauth2/authorize
https://{AuthorizationServer_base_url}/oauth2/authorize?&client_id=client_id&state=1648810292&redirect_uri={Client_redirect_url}&response_type=code&scope=read-ticket
| Parameter | Required | Description |
|---|---|---|
| client_id | YES | OAuth 2.0 Client ID. |
| redirect_uri | YES | One of the registered redirect URIs. |
| state | YES | Opaque string to associate the authentication request during the callback. |
| response_type | YES | Specifies that the application is requesting an authorization code grant. |
| scope | YES | Scope or permissions requested by the client (read, write, etc.). |
GET /oauth2/authorize
https://{AuthorizationServer_base_url}/oauth2/authorize?&client_id=client_id&state=1648810292&redirect_uri={Client_redirect_url}&response_type=code&scope=openid read-ticket&nonce=RGfvbrKJ9bhmflKdqZcxWA
| Parameter | Required | Description |
|---|---|---|
| client_id | YES | OAuth 2.0 Client ID. |
| redirect_uri | YES | One of the registered redirect URIs. |
| state | YES | Opaque string to associate the authentication request during the callback. |
| response_type | YES | Specifies the response the client is expecting from the Authorization Server. Must be code |
| scope | YES | Scope or permissions requested by the client (read, write, etc.). All OIDC flows must include openid in the scope. There must be a space separator between the actual scope definition(s) and "openid". |
| nonce | YES | A unique opaque string required specifically for OIDC requests. Nonce is generated by the client prior to sending an OIDC request. It is used to prevent replay attacks and also to verify the id_token received from the Authorization Server. |
Optionally, the Client may use Proof Key for Code Exchange also as known as PKCE. PKCE is an OAuth 2.0 security extension for public clients intended to avoid a malicious program from intercepting the authorization code.
PKCE is mandatory for all Public clients (using the code_challenge and code_challenge_method parameters) for an added layer of security.
For confidential clients who are able to perform private key authentication, PKCE is optional but recommended. It can be enforced for confidential clients by setting the fpx.oidc.provider.pkce.enforced value to 'true' when configuring the Authorization Server.
| Parameter | Required | Description |
|---|---|---|
| code_challenge | YES | The code challenge is a BASE64-URL-encoded string of the SHA256 hash of the code verifier |
| code_challenge_method | YES | The hash function used to generate code challenge from the code verifier. Must be S256. |
- FPX UMA 2.0
- OAuth 2.0
- OIDC
Sample Request using PKCE
https://{AuthorizationServer_base_url}/transaction/authorize?&ticket=exampleticket&client_id=exampleclient&state=randomvalue&claims_redirect_uri={Client_redirect_url}&code_challenge_method=S256&code_challenge=nxAvddK_1ECz_2oDLMevOnJbjPEBeNSEbdx96iuqVJg
Sample Request using PKCE
https://{AuthorizationServer_base_url}/oauth2/authorize?&client_id=client_id&state=1648810292&redirect_uri={Client_redirect_url}&response_type=code&scope=read-ticket&code_challenge_method=S256&code_challenge=nxAvddK_1ECz_2oDLMevOnJbjPEBeNSEbdx96iuqVJg
Sample Request using PKCE
https://{AuthorizationServer_base_url}/oauth2/authorize?&client_id=client_id&state=1648810292&redirect_uri={Client_redirect_url}&response_type=code&scope=openid read-ticket&nonce=RGfvbrKJ9bhmflKdqZcxWA&code_challenge_method=S256&code_challenge=nxAvddK_1ECz_2oDLMevOnJbjPEBeNSEbdx96iuqVJg
3. Client Callback and Authorization Code from the Authorization Server
When the Authorization Server processes the authorization request and it's been approved or denied by the user, the Authorization Server redirects the user agent to the client redirect URI.
- FPX UMA 2.0
- OAuth 2.0
- OIDC
When the user approves the authorization request, the service redirects the user-agent to the application redirect URI, which was specified during the client registration, along with a Permission ticket value.
A typical response would be as below based on the redirect URI passed in the authorize step above:
https://{Client_redirect_url}?ticket=361e4986-56b2-446f-9718-b3794305f388&state=1654029277
When the user approves the authorization request, the service redirects the user-agent to the application redirect URI, which was specified during the client registration, along with an Authorization Code.
A typical response would be as below based on the redirect URI passed in the authorize step above:
https://{Client_redirect_url}?code=361e4986-56b2-446f-9718-b3794305f388&state=1654029277
When the user approves the authorization request, the service redirects the user-agent to the application redirect URI, which was specified during the client registration, along with an Authorization Code.
A typical response would be as below based on the redirect URI passed in the authorize step above:
http://{Client_redirect_url}?code=90096d3b-50a9-42f0-9f56-6951469487f2&state=1654029277
4. Access Token Request
The client application requests an access token from the API by passing either the ticket or the authorization code that was returned during the callback along with the authentication details.
For the FPX UMA flow, the POST /transaction/token call is used.
For the OAuth flow or the OIDC flow the POST /oauth2/token call is used.
The client uses the FPX UMA ticket to make a back-channel request for the access tokens at the token endpoint that it can then use to request resources.
This endpoint requires authentication and two methods are supported by the Authorization Server.
It is strongly suggested for security reasons to use JWT authentication as no credentials need to be exchanged between parties. Verification is achieved through the verification of cryptographic signatures.
JWT Authentication
It is strongly suggested to make use of a library to handle the signing and verification of JWTs. See JWT Libraries for packages available in different languages.
To use JWT authentication, the Client must build a JWT containing a specific set of claims and signed with the private key that can be verified by the Authorization Server using the public key set provided during registration.
{
"iss": "exampleclient",
"sub": "exampleclient",
"aud": "https://{AuthorizationServer_base_url}/transaction/token",
"exp": 1619831987, // JWT expiry - should be a future timestamp
"iat": 1619826987, // JWT valid from - should be in the past
"jti": "abcdef123456" // must be unique per request
}
The Access Token Request and Refresh Token Request calls under the JWT Authentication method differ slightly for the FPX UMA flow and the OAuth 2.0 flow. Select the appropriate tab for more information.
- FPX UMA 2.0
- OAuth 2.0
- OIDC
For the FPX UMA flow, the POST /transaction/token call is used.
Access Token Request
Request Parameters (JSON Data)
| Parameter | Required | Description |
|---|---|---|
| grant_type | YES | must be 'urn:ietf:params:oauth:grant-type:uma-ticket' |
| ticket | YES | The OAuth 2.0 ticket received by the client's callback URI. Note: This not the same as the capability ticket originally sent by the client to the Authorization Server. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" --data '{
"grant_type": "urn:ietf:params:oauth:grant-type:uma-ticket",
"ticket": "226A2331-73FC-4087-9B07-56E41E49DA02",
"client_assertion_type": "urn:ietf:params:oauth:client-assertion-type:jwt-bearer",
"client_assertion": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRGf"
}'
If the initial request was made using PKCE, the token endpoint must also include the code verifier.
| Key | Required | Description |
|---|---|---|
| code_verifier | YES | The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" --data '{
"grant_type": "urn:ietf:params:oauth:grant-type:uma-ticket",
"ticket": "226A2331-73FC-4087-9B07-56E41E49DA02",
"client_assertion_type": "urn:ietf:params:oauth:client-assertion-type:jwt-bearer",
"client_assertion": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRGf",
"code_verifier":"C4ZrQS1sfnvUsJrrWhWLE3RukRwLcnfINKrLfyXqIBz"
}'
The client assertion JWT shown here is for demonstration purposes only and is not valid.
Refresh Token Request
The access tokens provided by the token endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token' |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" --data '{
"grant_type": "refresh_token",
"refresh_token": "226A2331-73FC-4087-9B07-56E41E49DA02",
"client_assertion_type": "urn:ietf:params:oauth:client-assertion-type:jwt-bearer",
"client_assertion": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRGf"
}'
For the OAuth flow, the POST /oauth2/token call is used.
Access Token Request
Request Parameters (JSON Data)
| Parameter | Required | Description |
|---|---|---|
| grant_type | YES | must be 'authorization_code' |
| redirect_uri | YES | https://{Client_base_url}/redirect |
| code | YES | Actual authorization code value. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiMDMyZTcyNDItOWFhYi00ZDkxLWI2NjYtZDcyMjgwMTU0MjkxIn0.ht8P5FeTze0-2Y-ISsmxTUaTF246weLxjvbfX4Zb3cfrpPmdW2trg6bGgfq8lBDtkOyPzmLFieUxkNtfZDpqYV6UgRtaVcqerCysEVLHHIaxa5mB7tfUQtBFzIidVDoPfvAEOmMowc6F7whH1IuOmDTp6szfm_uYEHZzLNEERm_bXr0R6uN-ig-l6bgVNsTvswtvRx7AtlvOb0B62FH1Kp4mLc7W8JoqMkowfV-UVXKoFFtIOQj6d9omwEHljWPY9BR_YtUVfkGzxTk1S3Ieax0tQT4Ke0ed9kPTviLKAD04D7lrRu2gpPAq4y8S1UEVshddQmDZEt7WlgmgDkK5pw'
If the initial request was made using PKCE, the token endpoint must also include the code verifier.
| Key | Required | Description |
|---|---|---|
| code_verifier | YES | The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/oauth2/token \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiMDMyZTcyNDItOWFhYi00ZDkxLWI2NjYtZDcyMjgwMTU0MjkxIn0.ht8P5FeTze0-2Y-ISsmxTUaTF246weLxjvbfX4Zb3cfrpPmdW2trg6bGgfq8lBDtkOyPzmLFieUxkNtfZDpqYV6UgRtaVcqerCysEVLHHIaxa5mB7tfUQtBFzIidVDoPfvAEOmMowc6F7whH1IuOmDTp6szfm_uYEHZzLNEERm_bXr0R6uN-ig-l6bgVNsTvswtvRx7AtlvOb0B62FH1Kp4mLc7W8JoqMkowfV-UVXKoFFtIOQj6d9omwEHljWPY9BR_YtUVfkGzxTk1S3Ieax0tQT4Ke0ed9kPTviLKAD04D7lrRu2gpPAq4y8S1UEVshddQmDZEt7WlgmgDkK5pw' \
--data-urlencode 'code_verifier=C4ZrQS1sfnvUsJrrWhWLE3RukRwLcnfINKrLfyXqIBz'
Refresh Token Request
The access tokens provided by the token endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token' |
| redirect_uri | YES | Redirect URI back to the client. {Client_redirect_url} |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'refresh_token=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiNjlhOTY0YWQtMjQ4Ni00NjEwLWI2MjItM2M1YjVlODJhNjA0In0.PmteD5RfMo_Ei7GdOKK3hAR2WP3ZcCoaU0R2KXGY1ZM'
For the OIDC flow, the POST /oauth2/token call is used.
Access Token Request
Request Parameters (JSON Data)
| Parameter | Required | Description |
|---|---|---|
| grant_type | YES | must be 'authorization_code' |
| redirect_uri | YES | https://{Client_base_url}/redirect |
| code | YES | Actual authorization code value. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiMDMyZTcyNDItOWFhYi00ZDkxLWI2NjYtZDcyMjgwMTU0MjkxIn0.ht8P5FeTze0-2Y-ISsmxTUaTF246weLxjvbfX4Zb3cfrpPmdW2trg6bGgfq8lBDtkOyPzmLFieUxkNtfZDpqYV6UgRtaVcqerCysEVLHHIaxa5mB7tfUQtBFzIidVDoPfvAEOmMowc6F7whH1IuOmDTp6szfm_uYEHZzLNEERm_bXr0R6uN-ig-l6bgVNsTvswtvRx7AtlvOb0B62FH1Kp4mLc7W8JoqMkowfV-UVXKoFFtIOQj6d9omwEHljWPY9BR_YtUVfkGzxTk1S3Ieax0tQT4Ke0ed9kPTviLKAD04D7lrRu2gpPAq4y8S1UEVshddQmDZEt7WlgmgDkK5pw'
If the initial request was made using PKCE, the token endpoint must also include the code verifier.
| Key | Required | Description |
|---|---|---|
| code_verifier | YES | The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/oauth2/token \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiMDMyZTcyNDItOWFhYi00ZDkxLWI2NjYtZDcyMjgwMTU0MjkxIn0.ht8P5FeTze0-2Y-ISsmxTUaTF246weLxjvbfX4Zb3cfrpPmdW2trg6bGgfq8lBDtkOyPzmLFieUxkNtfZDpqYV6UgRtaVcqerCysEVLHHIaxa5mB7tfUQtBFzIidVDoPfvAEOmMowc6F7whH1IuOmDTp6szfm_uYEHZzLNEERm_bXr0R6uN-ig-l6bgVNsTvswtvRx7AtlvOb0B62FH1Kp4mLc7W8JoqMkowfV-UVXKoFFtIOQj6d9omwEHljWPY9BR_YtUVfkGzxTk1S3Ieax0tQT4Ke0ed9kPTviLKAD04D7lrRu2gpPAq4y8S1UEVshddQmDZEt7WlgmgDkK5pw' \
--data-urlencode 'code_verifier=C4ZrQS1sfnvUsJrrWhWLE3RukRwLcnfINKrLfyXqIBz'
Refresh Token Request
The access tokens provided by the token endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token' |
| redirect_uri | YES | Redirect URI back to the client. {Client_redirect_url} |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
| client_assertion_type | YES | Must be set to 'urn:ietf:params:oauth:client-assertion-type:jwt-bearer'. |
| client_assertion | YES | JWT signed with private key containing required claims. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'refresh_token=df4ba24c-ebfb-43b8-90d9-64d90f7dd647' \
--data-urlencode 'client_assertion_type=urn:ietf:params:oauth:client-assertion-type:jwt-bearer' \
--data-urlencode 'client_assertion=eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJjbGllbnRfaWQiLCJhdWQiOiJ1cmx0aGluZ3MiLCJpc3MiOiJjbGllbnRfaWQiLCJleHAiOjE2NTQzMjE4MTMsImlhdCI6MTY1NDMwMDIxMywianRpIjoiNjlhOTY0YWQtMjQ4Ni00NjEwLWI2MjItM2M1YjVlODJhNjA0In0.PmteD5RfMo_Ei7GdOKK3hAR2WP3ZcCoaU0R2KXGY1ZM'
Shared Secret Authentication
While supported, OAuth Shared Secret is not recommended for production workloads. It can be useful for proof of concept or other internal purposes.
The Access Token Request and Refresh Token Request calls under the Shared Secret Authentication method differ slightly for the FPX UMA flow and the OAuth 2.0/OIDC flows. Select the appropriate tab for more information.
- FPX UMA 2.0
- OAuth 2.0
- OIDC
Access Token Request
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
Request Body
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'urn:ietf:params:oauth:grant-type:uma-ticket' |
| ticket | YES | The ticket (OAuth 2.0 auth_code) received by the client's callback URI. Note: This is not the same as the capability ticket originally sent by the client to the Authorization Server |
| code_verifier | NO | Required if the request was initiated using PKCE. The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" -H "Authorization: Basic dGVzdC1pZGVudG9zLWNsaWVudDp0asicZXN0LWlkZW50b3Mtc2VjcmV0" --data '{
"grant_type":"urn:ietf:params:oauth:grant-type:uma-ticket",
"ticket":"43fd5565-c722-4b89-983a-f05f10df1742"
}'
Sample Request with PKCE code Verifier
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" -H "Authorization: Basic dGVzdC1pZGVudG9zLWNsaWVudDp0asicZXN0LWlkZW50b3Mtc2VjcmV0" --data '{
"grant_type":"urn:ietf:params:oauth:grant-type:uma-ticket",
"ticket":"43fd5565-c722-4b89-983a-f05f10df1742",
"code_verifier":"7uciLUrALDEyeKgMzyfK7kzMkBpJPsw1CLXxoUtJtb9"
}'
Refresh Token Request
The access tokens provided at this endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token'. |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
Sample Request
curl -X POST https://{AuthorizationServer_base_url}/transaction/token -H "Content-Type: application/json" -H "Authorization: Basic dGVzdC1pZGVudG9zLWNsaWVudDp0asicZXN0LWlkZW50b3Mtc2VjcmV0" -H "Content-Type: application/json" --data '{
"grant_type": "refresh_token",
"refresh_token": "226A2331-73FC-4087-9B07-56E41E49DA02",
}'
Access Token Request
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
| Content-Type | YES | The Content-Type must be set to 'application/x-www-form-urlencoded'. This describes form data that is sent in a single block in the HTTP message body as outlined in the OAuth Specification. |
Request Body
| Key | Required | Description |
|---|---|---|
| grant_type | YES | authorization_code |
| code | YES | Actual authorization code used for verification of the request. |
| redirect_uri | YES | Redirect URI back to the client. {Client_redirect_url} |
| client_id (optional) | YES | Client identifier - a unique string representing the registration information provided by the client. |
| code_verifier | NO | The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. Required if the request was initiated using PKCE. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'client_id=client_id' \
--data-urlencode 'redirect_uri=https://{AuthorizationServer_base_url}/redirect' \
--data-urlencode 'code=361e4986-56b2-446f-9718-b3794305f388'
Sample Request with PKCE code Verifier
curl --location --request POST 'https://{authserver-base-url}/oauth2/token' \
--header 'Authorization: Basic cnNhX3B1Yl9jbGllbnRfaWM6cnNhX3B1Yl9jbGllbnRfc2VjcmV0' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'code=0cfaf1a1-30bf-4282-8daf-ef60a737aff9' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code_verifier=g2mDrjIjcLTybvZnmEHMDpX9jHasJpnL1pBG7LvaMUbVcPIp0q05ZDKRmUFmkiGa' \
--data-urlencode 'client_id=rsa_pub_client_ic' \
--data-urlencode 'code_verifier=C4ZrQS1sfnvUsJrrWhWLE3RukRwLcnfINKrLfyXqIBz'
Refresh Token Request
The access tokens provided at this endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
| Content-Type | YES | The Content-Type must be set to 'application/x-www-form-urlencoded'. This describes form data that is sent in a single block in the HTTP message body as outlined in the OAuth Specification. |
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token'. |
| client_id (optional) | YES | Client identifier - a unique string representing the registration information provided by the client. |
| redirect_uri | YES | https://{Client_base_url}/redirect |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
Sample Request
curl --location --request POST 'https://{authserver-base-url}/transaction/token' \
--header 'Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'client_id=client_id' \
--data-urlencode 'redirect_uri=https://{authserver-base-url}/redirect' \
--data-urlencode 'refresh_token=df4ba24c-ebfb-43b8-90d9-64d90f7dd647'
Access Token Request
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
| Content-Type | YES | The Content-Type must be set to 'application/x-www-form-urlencoded'. This describes form data that is sent in a single block in the HTTP message body as outlined in the OAuth Specification. |
Request Body
| Key | Required | Description |
|---|---|---|
| grant_type | YES | authorization_code |
| code | YES | Actual authorization code used for verification of the request. |
| redirect_uri | YES | Redirect URI back to the client. {Client_redirect_url} |
| client_id (optional) | YES | Client identifier - a unique string representing the registration information provided by the client. |
| code_verifier | NO | The code challenge in the initial authorized request is the BASE64-URL-encoded string of the SHA256 hash of the code verifier. Required if the request was initiated using PKCE. |
Sample Request
curl --location --request POST 'https://{AuthorizationServer_base_url}/oauth2/token' \
--header 'Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'client_id=client_id' \
--data-urlencode 'redirect_uri=https://{AuthorizationServer_base_url}/redirect' \
--data-urlencode 'code=361e4986-56b2-446f-9718-b3794305f388'
Sample Request with PKCE code Verifier
curl --location --request POST 'https://{authserver-base-url}/oauth2/token' \
--header 'Authorization: Basic cnNhX3B1Yl9jbGllbnRfaWM6cnNhX3B1Yl9jbGllbnRfc2VjcmV0' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'code=0cfaf1a1-30bf-4282-8daf-ef60a737aff9' \
--data-urlencode 'redirect_uri={Client_redirect_url}' \
--data-urlencode 'code_verifier=g2mDrjIjcLTybvZnmEHMDpX9jHasJpnL1pBG7LvaMUbVcPIp0q05ZDKRmUFmkiGa' \
--data-urlencode 'client_id=rsa_pub_client_ic' \
--data-urlencode 'code_verifier=C4ZrQS1sfnvUsJrrWhWLE3RukRwLcnfINKrLfyXqIBz'
Refresh Token Request
The access tokens provided at this endpoint will expire quickly. In order to receive new access tokens, a subsequent request to this endpoint should be made using the refresh token.
Request Headers
| Key | Required | Description |
|---|---|---|
| Authorization | YES | Base64 encoded string containing client id and secret separated by a colon as HTTP Basic Authorization token. |
| Content-Type | YES | The Content-Type must be set to 'application/x-www-form-urlencoded'. This describes form data that is sent in a single block in the HTTP message body as outlined in the OAuth Specification. |
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| grant_type | YES | Must be 'refresh_token'. |
| client_id (optional) | YES | Client identifier - a unique string representing the registration information provided by the client. |
| redirect_uri | YES | https://{Client_base_url}/redirect |
| refresh_token | YES | The refresh token received from a previous call to the token endpoint. |
Sample Request
curl --location --request POST 'https://{authserver-base-url}/transaction/token' \
--header 'Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'client_id=client_id' \
--data-urlencode 'redirect_uri=https://{authserver-base-url}/redirect' \
--data-urlencode 'refresh_token=df4ba24c-ebfb-43b8-90d9-64d90f7dd647'
Response
The JWTs used for access_token, id_token, and similar fields in the following examples is invalid and purely for illustrative purposes. A real JWT would typically be 4 Kb in length.
- FPX UMA 2.0
- OAuth 2.0
- OIDC
On successful authorization, the Authorization Server returns an access_token as a signed JWT. The Client should verify the signature using the Authorization Server's key set before processing the payload. The access token requires further processing before it can be used to request the resources granted by the user to the Client.
The access token response has the following claims:
Access Token Response Claims (FPX UMA 2.0)
| Claim | Description |
|---|---|
access_token | The JWT from the Authorization Server. The Client must process the JWT to uncover the authorized Resource Servers for each required resource. |
expires_in | Seconds before the token will expire. |
token_type | The access token type. Will be fpx:rpt.rs.location.token for UMA 2.0 flows. |
Sample Access Token Response (FPX UMA 2.0)
{
"access_token": "eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJleUowZVhBaU9pSktWMVFpTENKaGJHY2lPaUpJVXpJMU5pSjkuZXlKaGRXUWlPaUiJodHRwczpcL1wvYXV0aHNlcnZlci5mcHgtc3RhZ2luZy5kZXYuaWRlbnRvcy5jYSIsImV4cCI6MTYxOTgzMDMyMiwiaWF0IjoxNjE5ODMwMDIyfQ.nJwzc8wonnmUM8b6JglLJaWHEE9pLpKgZ5kt7rU1z6NCycr4K99QpcIH9QAoK8aB08OWawjmtGYmfp9tDxfgwilO6kV0qTRV6UTP1SAqxh_7sNVGA",
"expires_in": 259199,
"token_type": "fpx:rpt.rs.location.token"
}
When the JWT contained in access_token is decoded, it returns the following claims:
Decoded Access Token Claims (FPX UMA 2.0)
| Claim | Description | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
sub | (Subject) The resource owner token. | ||||||||||||||
aud | (Audience) The intended audience for the access token, in this case a Client ID. | ||||||||||||||
iss | (Issuer) The issuer of the access token, in this case the base URL of the Authorization Server. | ||||||||||||||
exp | (Expiration Time) The timestamp at which the access token will expire. | ||||||||||||||
iat | (Issued At) The timestamp at which the access token was issued. | ||||||||||||||
access_tokens[] | An array of access tokens, with one access token for each of the resources granted access to.
|
Sample Decoded Access Token (FPX UMA 2.0)
{
"sub": "43fd5565-c722-4b89-983a-f05f10df1742",
"aud": "test-identos-client",
"iss": "https://authserver.fpx-staging.dev.identos.ca",
"exp": 1620089222,
"iat": 1619830022,
"access_tokens": [
{
"access_token": "eyJraWQiOiJyc2ExIiwidHlwIjoiSldUIiwiYWxnIjoiUlMyNTYifQ.eyJzdWIiOiJleUowZVhBaU9pSktWMVFpTENKaGJHY2lPaUpJVXpJMU5pSjkuZXlKaGRXUWlPaUiJodHRwczpcL1wvYXV0aHNlcnZlci5mcHgtc3RhZ2luZy5kZXYuaWRlbnRvcy5jYSIsImV4cCI6MTYxOTgzMDMyMiwiaWF0IjoxNjE5ODMwMDIyfQ.nJwzc8wonnmUM8b6JglLJaWHEE9pLpKgZ5kt7rU1z6NCycr4K99QpcIH9QAoK8aB08OWawjmtGYmfp9tDxfgwilO6kV0qTRV6UTP1SAqxh_7sNVGA",
"refresh_token": "e6988f13-aa9e-421b-b1de-8abaf5484c34",
"resource_type": "https://www.identos.com/resource-definitions/identity-profile",
"resource_id": "id-profile",
"token_type": "bearer",
"expires_in": "299",
"resource_location": "https://idstore.rs.dev.identos.ca/auth/realms/user-portal/identity"
}
]
}
The OAuth 2.0 access_token retrieved from the Authorization Server does not need further processing and can be used directly against the Resource Server to retrieve information. This is unlike the token response received in the FPX UMA 2.0 flow, where the Client must first decode the access token in order to retrieve the bearer token.
The access token response has the following claims:
Access Token Response Claims (OAuth 2.0)
| Claim | Description |
|---|---|
access_token | The OAuth 2.0 token used against APIs to retrieve protected resources. |
refresh_token | The refresh token from the Authorization Server. |
token_type | The access token type. Will be bearer for OAuth 2.0 flows. |
expires_in | Seconds before the token will expire. |
scope | e.g. read, read-ticket, etc. |
Sample Access Token Response (OAuth 2.0)
{
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6IkJ1Y1IzaGNnNDNRWUhObjYxN2psUEtUZW1IS0J4aFg1dnpxZmx5MG9PSkNFVkIzWEl1NmNycVRReUFpR3RWMWIiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJyZWFkIl0sInR5cGUiOiJwZXJtaXNzaW9uIiwiZXhwIjoxNjU4MjMwNzMzLCJjbGllbnRfaWQiOiJvYXV0aF91bWFfY2xpZW50In0.FHWGOTFg0K06L1VhNasc-pKZ8OLCUB7clUbjwdSSIHs",
"expires_in": 3599,
"token_type": "Bearer",
"refresh_token": "e0dd0169-36a9-4cf4-b30a-3b78c6162bc3",
"scope": "read"
}
When the JWT contained in access_token is decoded, it returns the following claims:
Decoded Access Token Claims (OAuth 2.0)
| Claim | Description | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
sub | (Subject) The resource owner token. | ||||||||||
aud | (Audience) The base URL of the Resource Server. | ||||||||||
permissions[] | An array of permissions (TBD)
| ||||||||||
azp | (Authorized Parties) Must be the OAuth Client ID. | ||||||||||
iss | (Issuer) The issuer of the access token, in this case the base URL of the Authorization Server. | ||||||||||
exp | (Expiration Time) The timestamp at which the access token will expire. | ||||||||||
iat | (Issued At) The timestamp at which the access token was issued. |
Sample Decoded Access Token (OAuth 2.0)
{
"sub": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6IkJ1Y1IzaGNnNDNRWUhObjYxN2psUEtUZW1IS0J4aFg1dnpxZmx5MG9PSkNFVkIzWEl1NmNycVRReUFpR3RWMWIiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJyZWFkIl0sInR5cGUiOiJwZXJtaXNzaW9uIiwiZXhwIjoxNjU4MjMwNzMzLCJjbGllbnRfaWQiOiJvYXV0aF91bWFfY2xpZW50In0.FHWGOTFg0K06L1VhNasc-pKZ8OLCUB7clUbjwdSSIHs",
"aud": "http://localhost:8086",
"permissions": [
{
"sub": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6IkJ1Y1IzaGNnNDNRWUhObjYxN2psUEtUZW1IS0J4aFg1dnpxZmx5MG9PSkNFVkIzWEl1NmNycVRReUFpR3RWMWIiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJyZWFkIl0sInR5cGUiOiJwZXJtaXNzaW9uIiwiZXhwIjoxNjU4MjMwNzMzLCJjbGllbnRfaWQiOiJvYXV0aF91bWFfY2xpZW50In0.FHWGOTFg0K06L1VhNasc-pKZ8OLCUB7clUbjwdSSIHs",
"resource_scopes": [
"read"
],
"resource_type": "https://openid.net/specs/openid-connect-core-1_0.html",
"resource_id": "openid",
"exp": 1661229987
}
],
"azp": "oauth_client_id",
"iss": "http://localhost:8081",
"exp": 1658233605,
"iat": 1658230005
}
The OAuth-OIDC access_token retrieved from the Authorization Server does not need further processing and can be used directly against the Resource Server to retrieve information. This is unlike the token response received in the FPX UMA 2.0 flow, where the Client must first decode the access token in order to retrieve the bearer token.
Additionally, the OAuth-OIDC access token response also returns an id_token that can be decoded.
The access token response has the following claims:
Access Token Response Claims (OIDC)
| Claim | Description |
|---|---|
access_token | The OAuth 2.0 token used against APIs to retrieve protected resources. |
expires_in | Seconds before the token will expire. |
token_type | The access token type. Will be Bearer for OAuth 2.0 flows. |
refresh_token | The refresh token from the Authorization Server. |
id_token | An encoded JSON Web token (JWT) that ascertains the user has been authenticated with an Identity provider. The token is encoded in Base64 format and, when decoded, provides claims that serve as declarations about the user. |
scope | e.g. read-ticket |
Sample Access Token Response (OIDC)
{
"access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6IkJ1Y1IzaGNnNDNRWUhObjYxN2psUEtUZW1IS0J4aFg1dnpxZmx5MG9PSkNFVkIzWEl1NmNycVRReUFpR3RWMWIiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJyZWFkIl0sInR5cGUiOiJwZXJtaXNzaW9uIiwiZXhwIjoxNjU4MjMwNzMzLCJjbGllbnRfaWQiOiJvYXV0aF91bWFfY2xpZW50In0.FHWGOTFg0K06L1VhNasc-pKZ8OLCUB7clUbjwdSSIHs",
"expires_in": 3599,
"token_type": "Bearer",
"refresh_token": "65200e7a-e73b-4fb0-8c7e-8a12f6baa792",
"id_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6IkJ1Y1IzaGNnNDNRWUhObjYxN2psUEtUZW1IS0J4aFg1dnpxZmx5MG9PSkNFVkIzWEl1NmNycVRReUFpR3RWMWIiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJyZWFkIl0sInR5cGUiOiJwZXJtaXNzaW9uIiwiZXhwIjoxNjU4MjMwNzMzLCJjbGllbnRfaWQiOiJvYXV0aF91bWFfY2xpZW50In0.FHWGOTFg0K06L1VhNasc-pKZ8OLCUB7clUbjwdSSIHs",
"scope": "openid read"
}
When the JWT contained in access_token is decoded, it returns the following claims:
Decoded Access Token Claims (OIDC)
| Claim | Description | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
sub | (Subject) The resource owner token. | ||||||||||
aud | (Audience) Must be the Client ID. | ||||||||||
permissions[] | An array of permissions associated with the access token.
| ||||||||||
azp | (Authorized Parties) Must be the OAuth Client ID. | ||||||||||
iss | (Issuer) The issuer of the access token, in this case the base URL of the Authorization Server. | ||||||||||
exp | (Expiration Time) The timestamp at which the access token will expire. | ||||||||||
iat | (Issued At) The timestamp at which the access token was issued. |
Sample Decoded Access Token (OIDC)
{
"sub": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6ImRhNWM2SXhtNXhpVkNSM1loOGVta3RLYXhWYVZhT3EzcFZPazJpUUxtenU0dk5tRmdWUHBFRXlMVmIwZERjVVQiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJvcGVuaWQiXSwidHlwZSI6InBlcm1pc3Npb24iLCJleHAiOjE2NTgyMjM4NzMsImNsaWVudF9pZCI6ImtleWNsb2FrY191bWFfY2xpZW50In0.z1fG4y4u5cF3uLmdN28zzLukQmJt4-OWNBCE7--Pm70",
"aud": "http://localhost:8086",
"permissions": [
{
"sub": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6ImRhNWM2SXhtNXhpVkNSM1loOGVta3RLYXhWYVZhT3EzcFZPazJpUUxtenU0dk5tRmdWUHBFRXlMVmIwZERjVVQiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJvcGVuaWQiXSwidHlwZSI6InBlcm1pc3Npb24iLCJleHAiOjE2NTgyMjM4NzMsImNsaWVudF9pZCI6ImtleWNsb2FrY191bWFfY2xpZW50In0.z1fG4y4u5cF3uLmdN28zzLukQmJt4-OWNBCE7--Pm70",
"resource_scopes": [
"openid"
],
"resource_type": "https://openid.net/specs/openid-connect-core-1_0.html",
"resource_id": "openid",
"exp": 1661222165
}
],
"azp": "fpx-client",
"iss": "http://localhost:8081",
"exp": 1658226243,
"iat": 1658222643
}
When the JWT contained in id_token is decoded, it has the following claims (will vary based on token type):
Decoded ID Token Claims (OIDC)
| Claim | Description | ||
|---|---|---|---|
sub | (Subject) The resource owner's identifier. | ||
aud | (Audience) Must be the Client ID. | ||
permissions[] | An array of permissions associated with the ID token.
| ||
iss | (Issuer) The issuer of the access token, in this case the base URL of the Authorization Server. | ||
exp | (Expiration Time) The timestamp at which the access token will expire. | ||
nonce | Unique string value used to associate the ID Token with a Client session. | ||
iat | (Issued At) The timestamp at which the access token was issued. |
Sample Decoded ID Token (OIDC)
{
"sub": "0a48f509-f428-46c6-8eb9-4d9609c016fb",
"aud": "fpx-client",
"permissions": {
"openid": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJhdWQiOiJodHRwOlwvXC9sb2NhbGhvc3Q6ODA4NiIsInN1YiI6ImRhNWM2SXhtNXhpVkNSM1loOGVta3RLYXhWYVZhT3EzcFZPazJpUUxtenU0dk5tRmdWUHBFRXlMVmIwZERjVVQiLCJyZXNvdXJjZV9vd25lciI6IjBhNDhmNTA5LWY0MjgtNDZjNi04ZWI5LTRkOTYwOWMwMTZmYiIsImlzcyI6Imh0dHA6XC9cL2xvY2FsaG9zdDo4MDg0IiwicmVzb3VyY2VfaWQiOiJvcGVuaWQiLCJncmFudGVkX3Njb3BlcyI6WyJvcGVuaWQiXSwidHlwZSI6InBlcm1pc3Npb24iLCJleHAiOjE2NTgyMjM4NzMsImNsaWVudF9pZCI6ImtleWNsb2FrY191bWFfY2xpZW50In0.z1fG4y4u5cF3uLmdN28zzLukQmJt4-OWNBCE7--Pm70"
},
"iss": "http://localhost:8081",
"exp": 1658226243,
"nonce": "RGfvbrKJ9bhmflKdqZcxWA",
"iat": 1658222643
}
Failure Response
If an error occurs, or if an end user doesn't grant access to the Client, the Authorization Server will return an error code (error) and error description (error_description) to the Client.
Sample Failure Response
{
"error": "request_denied",
"error_description": "request was denied, no permissions granted"
}
Resource Server API
Once the Client has an access token and locations representing the requested resources, interactions between the Client and RS are largely out of scope. When making requests to/for protected resources, the Client MUST include the correct Bearer token from within the Access Token Payload.
| Header | Required | Description |
|---|---|---|
| Authorization | YES | OAuth 2.0 Bearer Token. |
The response will vary depending on the individual resource scope. See the details for the specific resource type that is being requested.
It is important to note that at any time the end user who has granted resources has the ability to revoke access to resources for any one client. In this case it may be required to re-ask the user to provide authorization to these resources again and starting the flow over.
Token Revocation
Token Revocation enables clients to revoke an access token they no longer need. Token Revocation disables the submitted token, refresh token, and any other associated access tokens that are issued. Once a token gets revoked, it will no longer serve to access the Resource Server API, as the token will fail introspections at the Authorization Server.
A client can revoke a token by sending an access token or the associated refresh token to the defined endpoint, that is POST /oauth2/token/revoke
The endpoint requires client authentication - either JWT or Shared Secret Authentication as described above.
Request Parameters (JSON Data)
| Key | Required | Description |
|---|---|---|
| token | YES | An access token or refresh token that is retrieved from the token endpoint |
| token_type_hint | Sometimes | Must be one of: 'access_token', 'refresh_token', or 'fpx:rpt.rs.location.token'. Only required if token value being revoked is the top-level token returned by the FPX UMA 2.0 token response (type is 'fpx:rpt.rs.location.token') |
When revoking a token of type fpx:rpt.rs.location.token, it is required to provide the token_type_hint. This hint corresponds to the top-level token returned by the FPX UMA 2.0 token response. The RPTs nested in that top-level token may be revoked without a hint, or using the access_token hint
Sample Request
curl --location --request POST 'https://{authserver-base-url}/oauth2/token/revoke' \
--header 'Authorization: Basic Y2xpZW50X2lkOmNsaWVudF9zZWNyZXQ=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'token=<TOKEN VALUE>' \
--data-urlencode 'token_type_hint=access_token'
Response
On successful revocation, the Authorization Server returns a '200' status code.